Post 003: The one about mobile device preservation at the moment of seizure.
by Chris Atha
Cue the old adage of wearing many hats. Much like the mad hatter of Lewis Carroll's 1865 and likely more popular Disney's Alice in Wonderland; I wear a hat or two. Though, one of the most common hats I wear now is that of an advisor, it’s a tiny little hat, which based only upon words would be much better suited as a visor. I digress to the topic at hand mobile devices, and what to do with them. Curiouser and curiouser.

Just as Ricky couldn’t quite figure out what to do with his hands, the question I want to address and discuss is. Upon seizure (Meaning the moment when we get our grabbers on it), what do we do, and more importantly why does it matter. A quick consult of SWGDE’s Best Practices for Mobile Devices Evidence Collection & Preservation Handling and Acquisition, gives us a handy dandy chart. The specific part to discuss today is the concept seen below known as “Network Isolation”. Which is defined in the aforementioned document as:“Network Isolation: To reduce the potential of remote wipes or receipt of additional data,
place the mobile device in a Radio Frequency (RF) blocking container such as a Faraday
bag, box, or room, or use another signal-blocking method to reduce or prevent network
Connectivity.”Simple enough. Though how often are we, and yes I’m lumping myself into this collective. How often do we abide by this with trusted and verified processes and procedures?
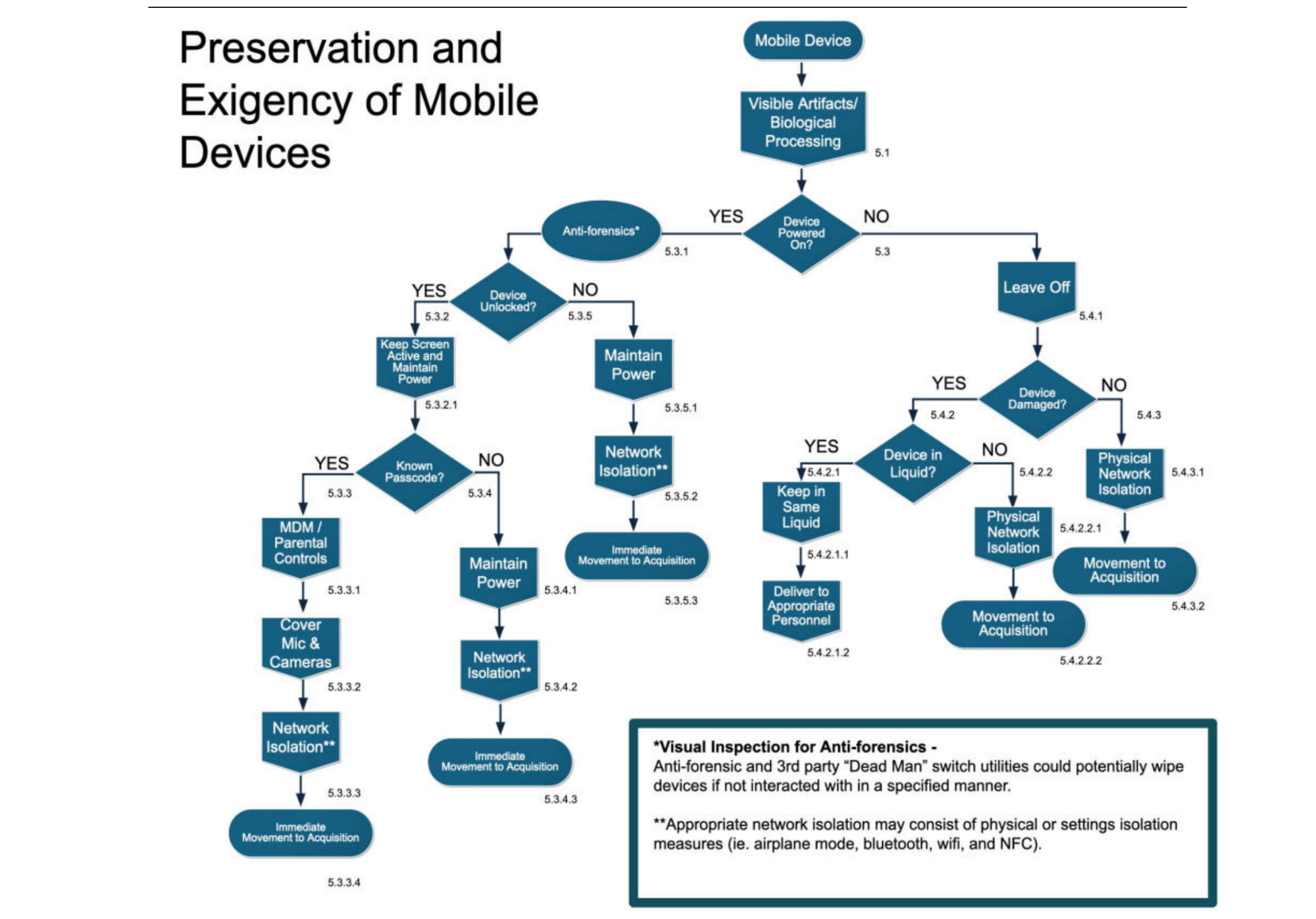
Simple enough. Though how often are we, and yes I’m lumping myself into this collective. How often do we abide by this with trusted and verified processes and procedures?And if we do not, why do we not? Hear me, I’m curious, and what this to be a discussion. Comment below on the Google form below.